Conventional Encryption Is a Term Used to Describe ______________ Encryption
The complexity of encryption methods has been successively increasing ever since. Its purpose is to ensure privacy by keeping the information hidden from anyone for whom it is not intended even those who can see the encrypted data.

All About Ssl Cryptography Digicert Com Cryptography Encryption Algorithms Ssl
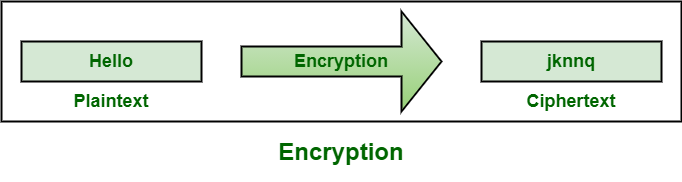
Encryption is a way of scrambling data so that only authorized parties can understand the information.

. Terms in this set 30 T or F Public key algorithms are useful in the exchange of conventional encryption keys. This process converts the original representation of the information known as plaintext into an alternative form known as ciphertext. System is referred to as symmetric single-key secret-key or conventional encryption.
Encryption is the transformation of data into a form unreadable by anyone without a secret decryption key. Larger context and generally provides protection against message modification only. Ciphertext is the scrambled message produced as output.
Here are some of the common encryption methods that you might see used in various encryption tools. Amount of information to work with. Perceptual encryption is a term used to describe various applications of encryption methods intended for audio speech image and video data.
Conventional encryption is a cryptographic system that uses the same key used by the sender to encrypt the message and by the receiver to decrypt the message. Enigma substitution transposition one-time pad Explanation. In this encryption method both the sender and the receiver use the same single key.
Different keys are used for encryption and decryption. Encryption does not itself prevent interference but denies the. Ideally only authorized parties can decipher a ciphertext back to plaintext and access the original information.
Public key cryptography is an encryption system which is based on two pairs of keys. Encryption is one of the most widely used and successful data protection technologies in todays corporate world. The naïve approach is a type of full encryption ap- after the encryption step belong to this class of algorithms.
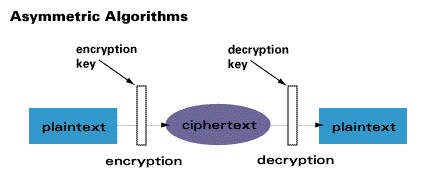
If the sender and receiver use different keys the system is referred to as asymmetric two-key or public-key encryption. Private key encryption is used to produce digital signatures which provide an enhanced form of message authentication. In public key encryption the sender and the receiver use different keys.
Public key is available to anyone while the secret key is only made available to the receiver of the message. Up to 24 cash back Symmetric single key secret key or conventional encryption. This class of algorithms includes the so-called naïve tion approaches that preserve the video compression format approach.
Terms in this set 30 1. ____ Authenticated encryption _____ is a term used to describe encryption systems that simultaneously protect confidentiality and authenticity integrity of communications. Public key algorithms are useful in the exchange of conventional encryption keys.
In secret key encryption every bit added doubles on average the time taken to break a piece of encrypted information breaking is a term used to describe recovering encrypted information. In this encryption model the sender encrypts the plaintext using the receivers secret key which can be later used by the receiver to. The key is used for both encryption and decryption purposes.
Encryption is a critical tool for maintaining data integrity and its importance cannot be overstated. In cryptography encryption is the process of encoding information. T or F The two important aspects of encryption are to verify that the contents of the.
This is a property which set this scheme different than symmetric encryption scheme. Advanced Encryption Standard AES Advanced Encryption Standard is a symmetric encryption algorithm that encrypts fixed blocks of data of 128 bits at a time. In simpler terms encryption takes readable data and alters it so that it appears random.
T or F The strength of a hash function against brute-force attacks depends solely on the length of the hash code produced by the algorithm. Proach in which a conventional cryptosystem is used in the encryption step. Data that has not been encrypted is referred to as plaintext and data that has been encrypted is referred to as ciphertext.
Ciphertext can be created by using the following. Modern protocols will use a private key for encryption and a different public key for decryption. A block cipher processes the.
The basic idea is that one performs encryption for multimedia content in a way that only a certain amount of perceptual information is touched by the encryption. Asymmetric encryption uses 2 pairs of key for encryption. Transposition letters are rearranged Substitution letters are replaced One-time pad.
It may be considered as intentionally degrading the quality of the multimedia. The key algorithmic ingredients of _____ CCM _____ are the AES encryption algorithm the CTR mode of operation and the CMAC authentication algorithm. Public keys are used to encrypt messages for a receiver.
The process of encryption and decryption is depicted in the following illustration. It is still much preferred of the two types of encryption systems due to its simplicity. The keys used to decipher the text can be 128- 192- or 256-bit long.
Conventional encryption ciphers rely on a single key for both encryption and decryption. Asymmetric two key or public key encryption. It was the only type of encryption in use prior to the development of public-key encryption.
Since ancient times various methods have been used to transform readable contentknown as plaintextinto a non-readable form. Conventional encryption also referred to as symmetric encryption or single-key encryption is a cryptographic system which uses the same key used by the sender to encrypt the message and by the receiver to decrypt the message. The term encryption is commonly used to describe techniques that are intended to protect information from unauthorized access.
Cybersecurity Essentials 11 Chapter 4 Quiz Answers 100 2018 What is the name of the method in which letters are rearranged to create the ciphertext. The most important properties of public key encryption scheme are. The advantage of a block cipher is that you can reuse keys.
The way in which the plaintext is processed. Viruses and worms are two examples of software attacks. In technical terms it is the process of converting human-readable plaintext to incomprehensible text also known as ciphertext.

What Types Of Encryption Are There Ico

Public Key Cryptography Cryptography Programmer Humor Coders Humor

Demystifying Symmetric And Asymmetric Encryption Cyber Security Encryption Cryptography
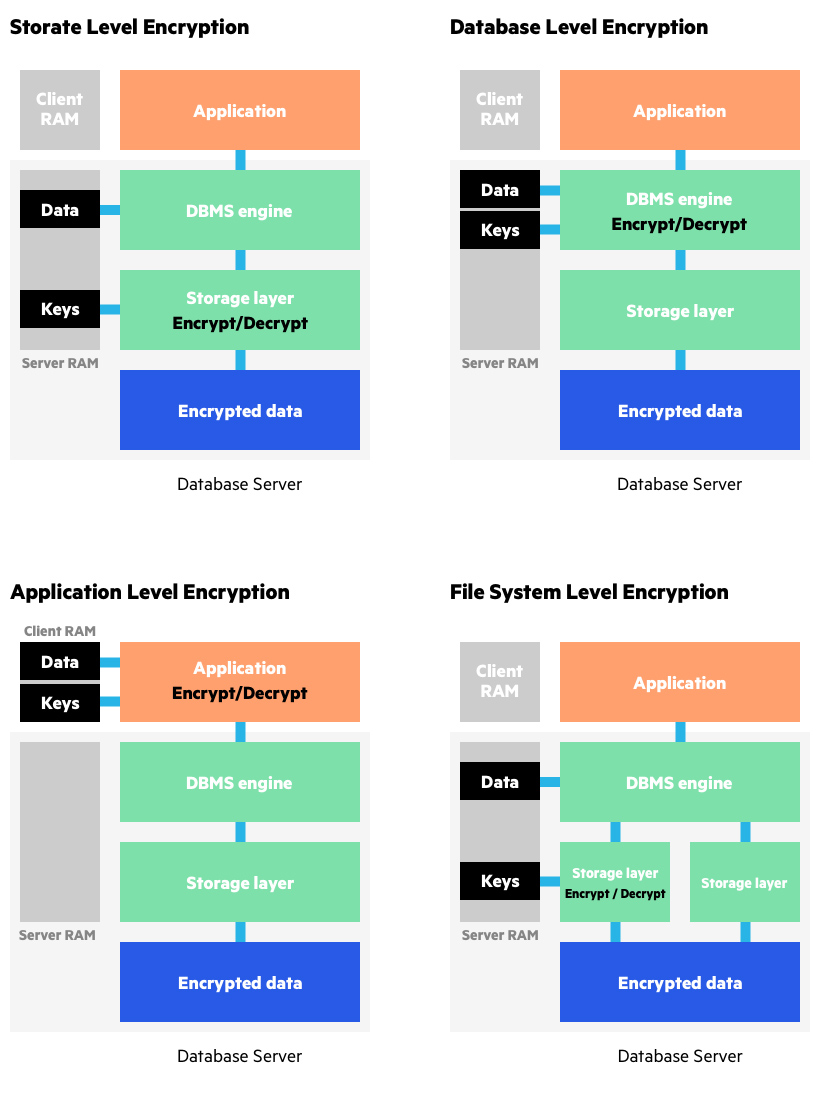
What Is Data Encryption From Des To Modern Algorithms Imperva

What Is Encryption Types Algorithms Practices Proofpoint Au
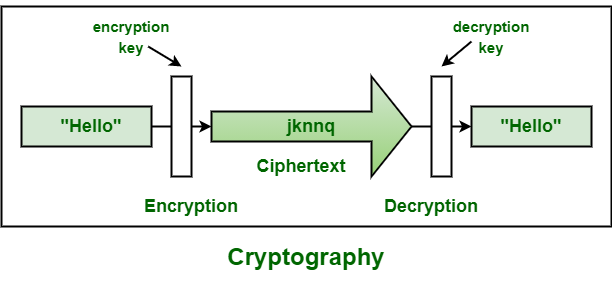
Difference Between Encryption And Cryptography Geeksforgeeks

Symmetric Vs Asymmetric Encryption 101 Computing

Symmetric Vs Asymmetric Encryption What Are Differences Cryptography Symmetric Cryptography Cyber Security Awareness

Types Of Encryption Symmetric Or Asymmetric Rsa Or Aes The Missing Report

The Key Differences Between Symmetric Vs Asymmetric Encryption Encryption Cyber Security Awareness Algorithm

Symmetric Encryption Encryption Safe Internet Wireless Router

Symmetric Vs Asymmetric Cryptography Cryptography Software Security Symmetric Cryptography

Difference Between Encryption Algorithms Algorithm Cryptography

Beginner S Guide To The Basics Of Data Encryption Infosec Resources
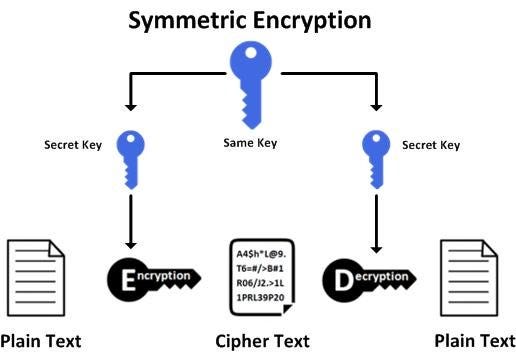
Encryption Methods In Today S Conditions We Provide Data By Minecakir The Startup Medium
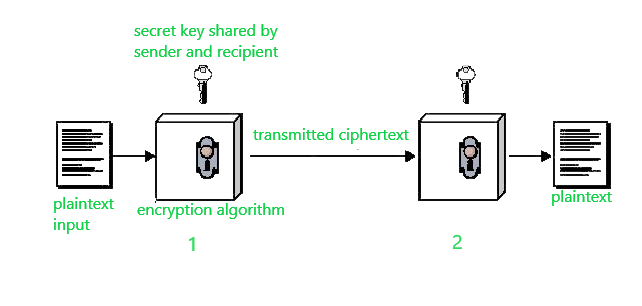
Conventional Encryption Geeksforgeeks
Cryptography Defined Brief History
Difference Between Encryption And Cryptography Geeksforgeeks
